Malware analysis
Por um escritor misterioso
Descrição

Figure .: Pros and Cons of Malware Analysis Methods
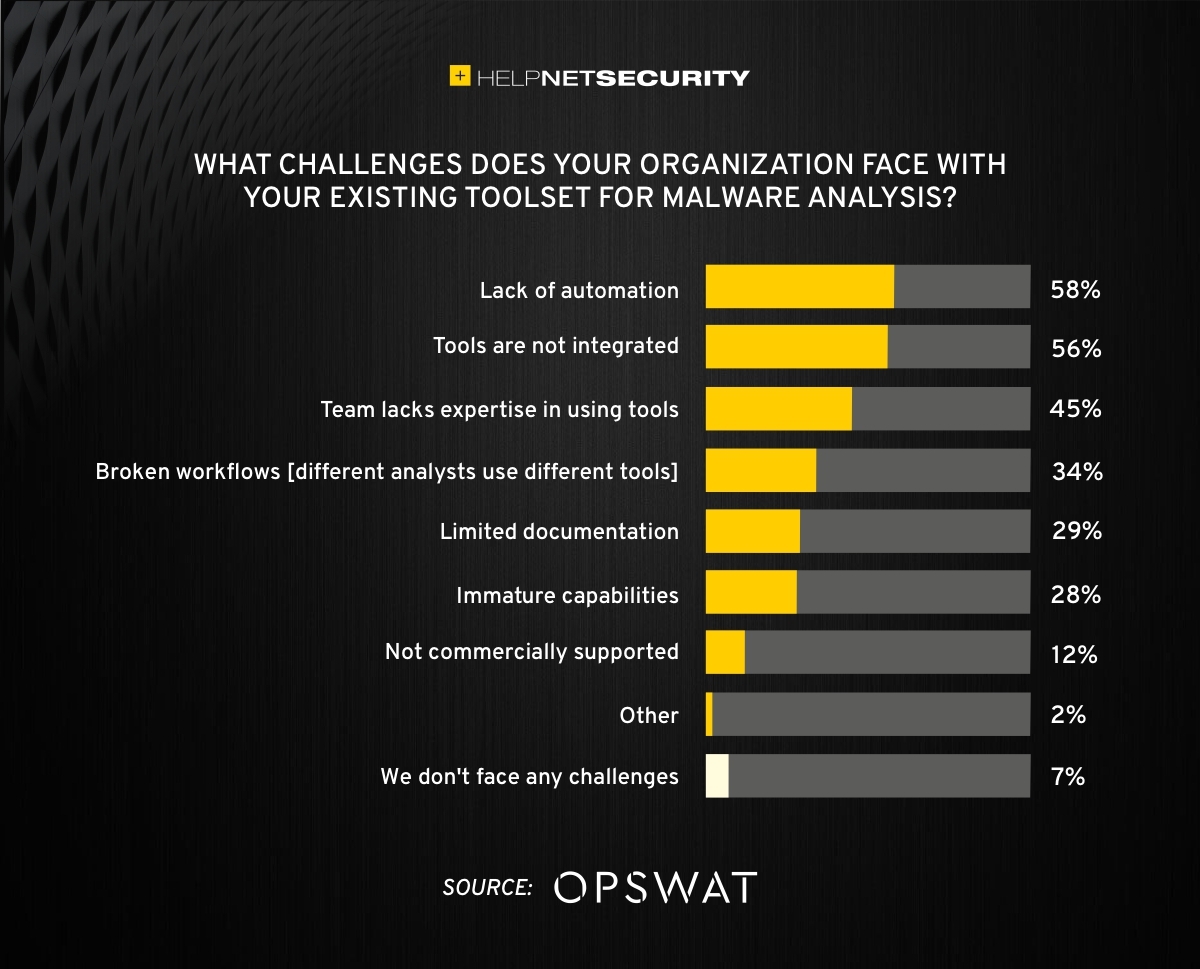
What is challenging malware analysis? - Help Net Security
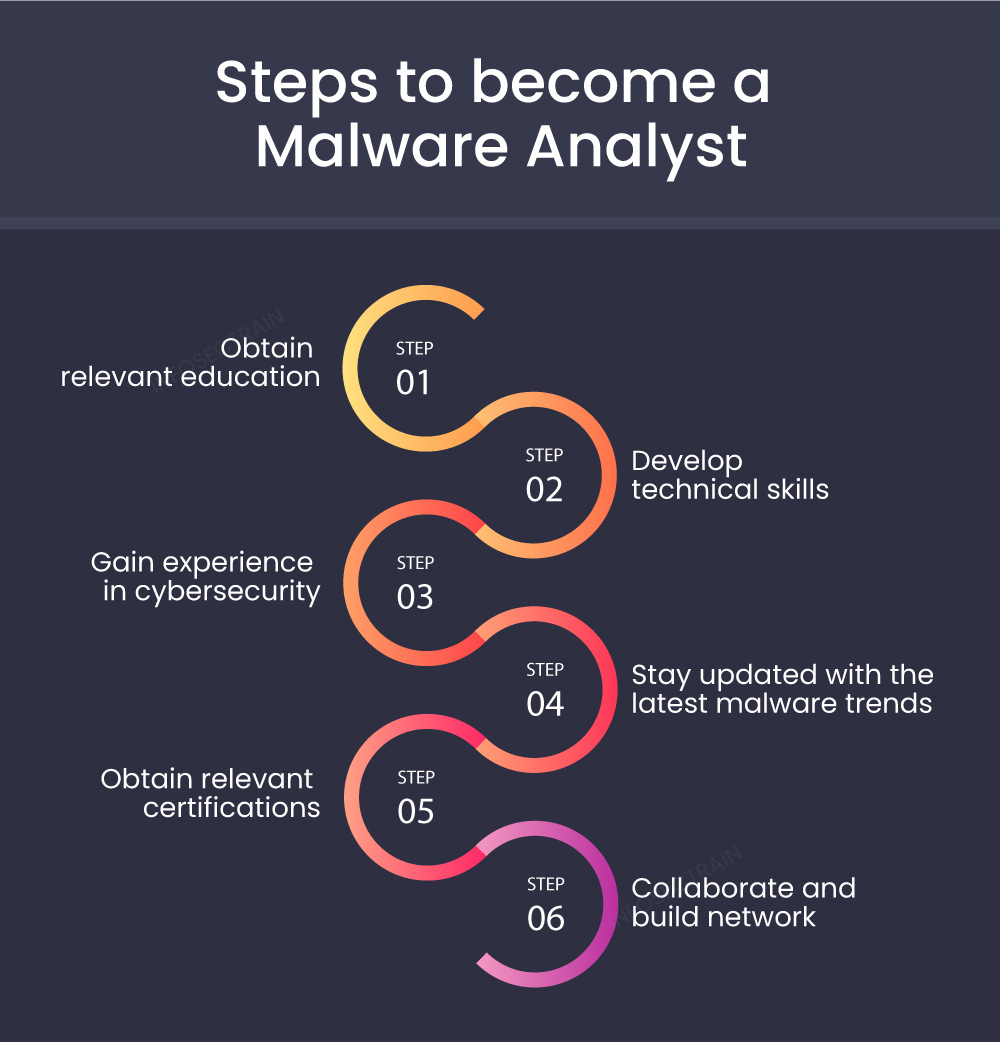
How to become a Malware Analyst? - InfosecTrain

A basic malware analysis method - ScienceDirect

Malware Analysis Explained - 's Cybersecurity Blog

PDF] Automated Malware Analysis using Python
Automated Malware Analysis with Low-Code Security Automation
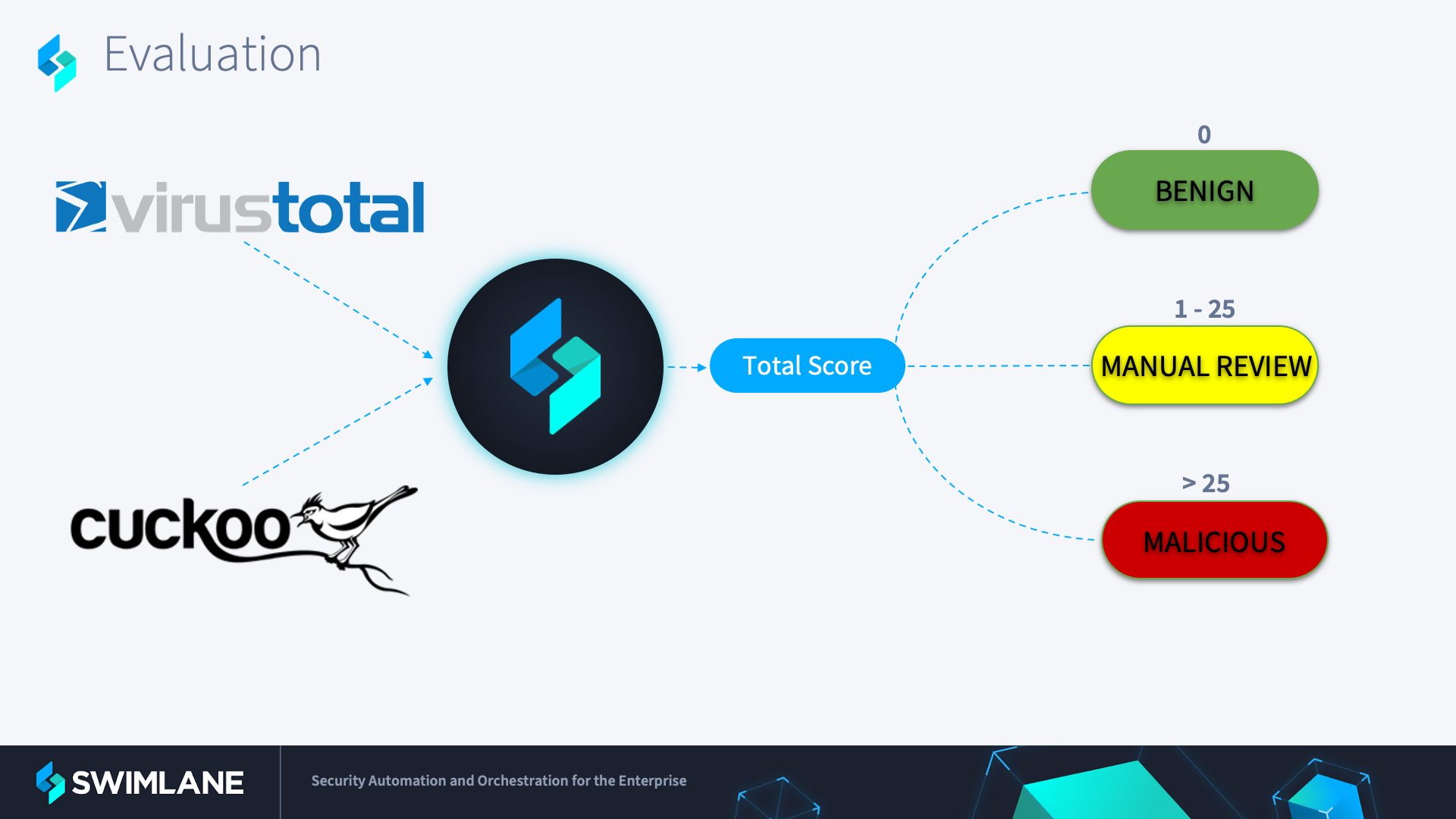
Automated Malware Analysis with Low-Code Security Automation

What to Include in a Malware Analysis Report

Security Orchestration Use Case: Automating Malware Analysis - Palo Alto Networks Blog
de
por adulto (o preço varia de acordo com o tamanho do grupo)





