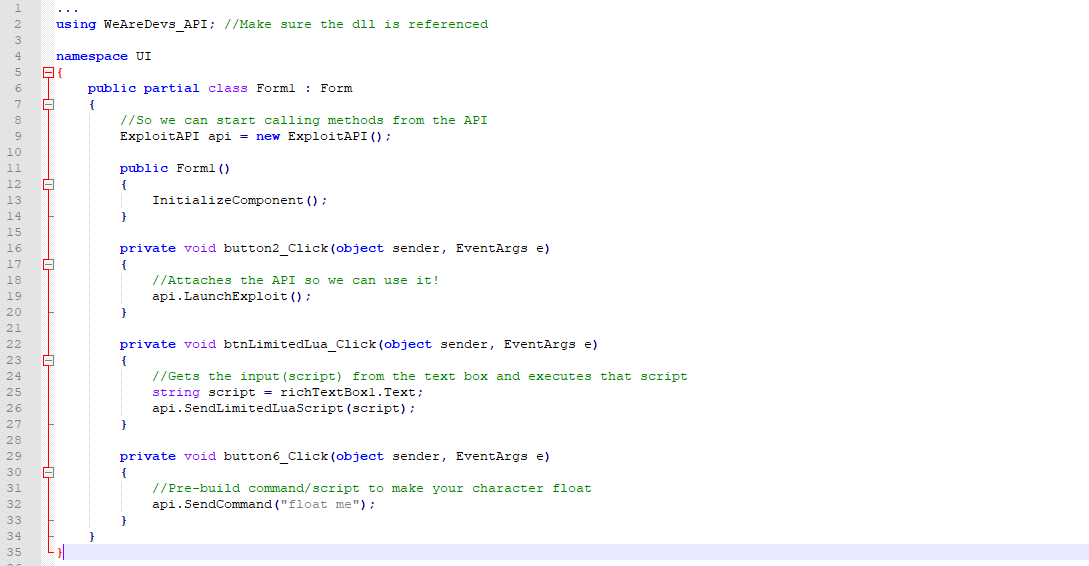
Malware analysis Malicious activity
Por um escritor misterioso
Descrição
Interactive Online Malware Sandbox
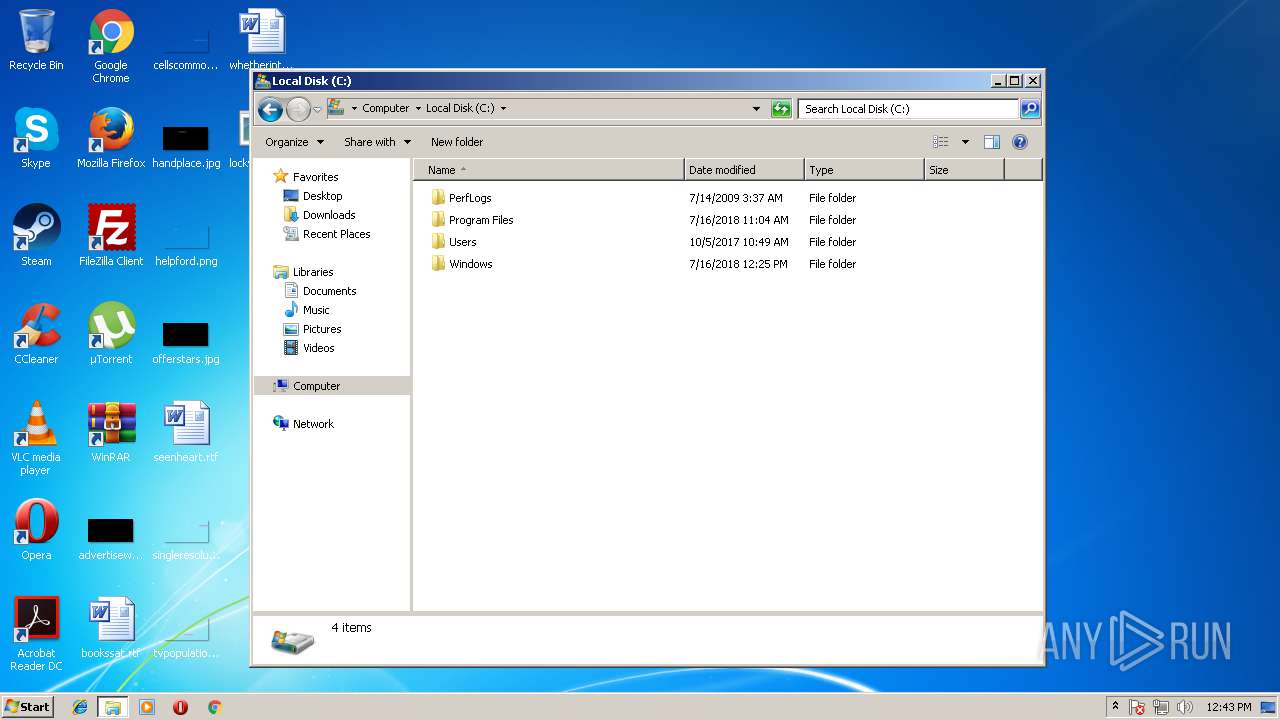
Malware analysis lockysample.bin.zip Malicious activity
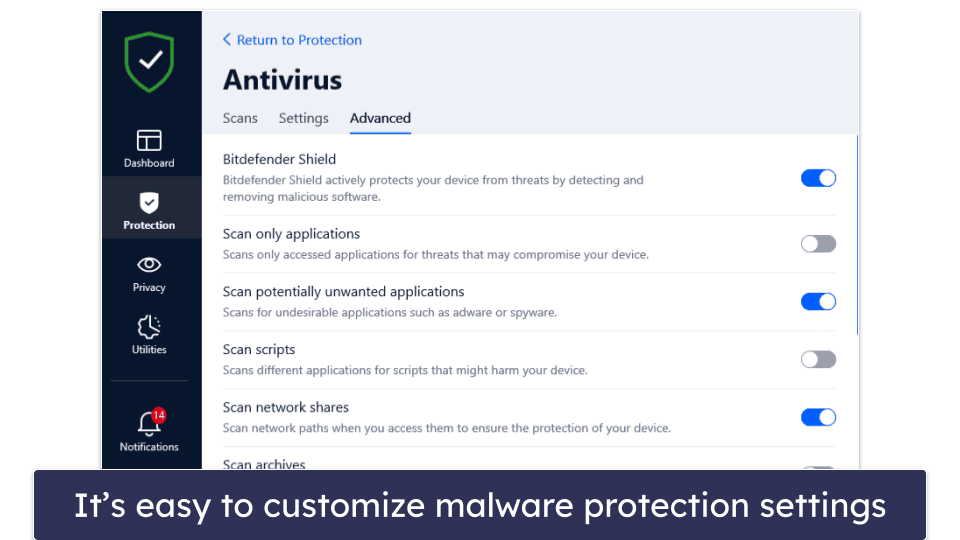
10 Best Antivirus Software in 2023: Windows, Android, iOS, Mac

Malware Analysis: Steps & Examples - CrowdStrike

Routers Roasting on an Open Firewall: the KV-botnet Investigation

FBI, CISA, MS-ISAC release cybersecurity advisory on emerging

Malware - Wikipedia
Malware analysis

Routers Roasting on an Open Firewall: the KV-botnet Investigation
de
por adulto (o preço varia de acordo com o tamanho do grupo)