Malware analysis Malicious activity
Por um escritor misterioso
Descrição

Routers Roasting on an Open Firewall: the KV-botnet Investigation

PROUD-MAL: static analysis-based progressive framework for deep

Malware Analysis: Steps & Examples - CrowdStrike

A detailed analysis of the Menorah malware used by APT34
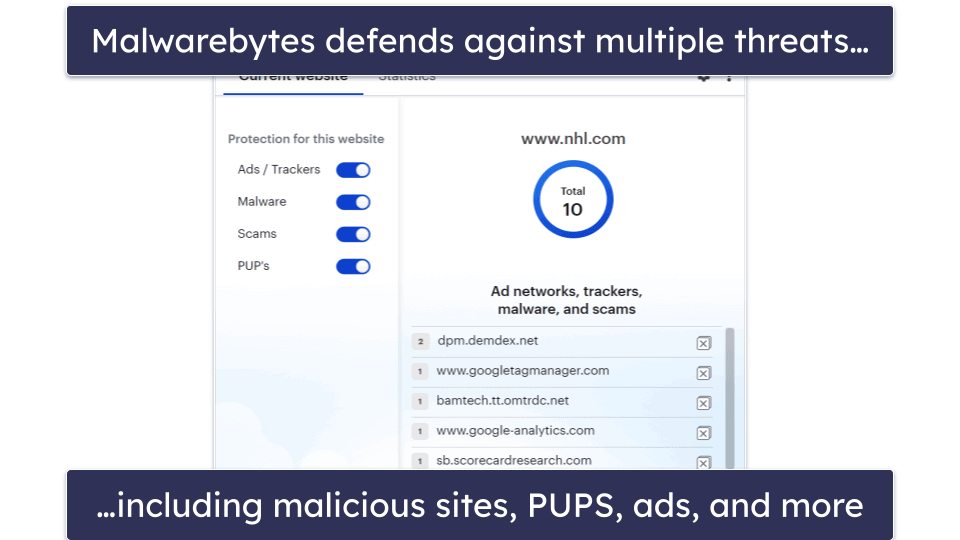
10 Best (REALLY FREE) Antivirus Software for Windows in 2023

Robust Malware Detection Models: Learning From Adversarial Attacks

Dynamic malware analysis [34]

Routers Roasting on an Open Firewall: the KV-botnet Investigation

Interactive Online Malware Sandbox

How to build a malware analysis sandbox with Elastic Security
de
por adulto (o preço varia de acordo com o tamanho do grupo)






/i.s3.glbimg.com/v1/AUTH_08fbf48bc0524877943fe86e43087e7a/internal_photos/bs/2019/9/I/3DNIt9SrK8m9Cn5kxm1w/steam-remote-play-together-1.jpg)