Malware analysis generator-no-survey-no-human-verification-2022-01-12 Malicious activity
Por um escritor misterioso
Descrição
Malware analysis generator-no-survey-no-human-verification-2022-01-12 Malicious activity
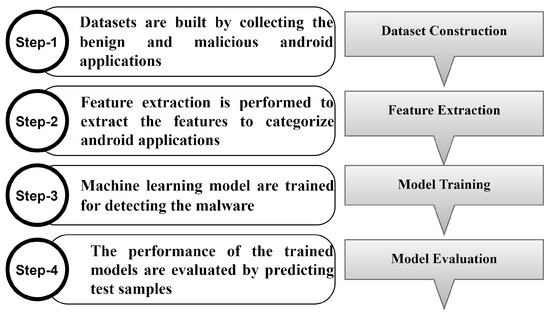
Sensors, Free Full-Text
Dallas Invents: 121 Patents Granted for Week of April 26 » Dallas Innovates

PDF) Survey on the Usage of Machine Learning Techniques for Malware Analysis

Machine learning in cybersecurity: a comprehensive survey - Dipankar Dasgupta, Zahid Akhtar, Sajib Sen, 2022

Malware Analysis: Steps & Examples - CrowdStrike

Technical Reviews Sumitomo Electric

Computer security - Wikipedia
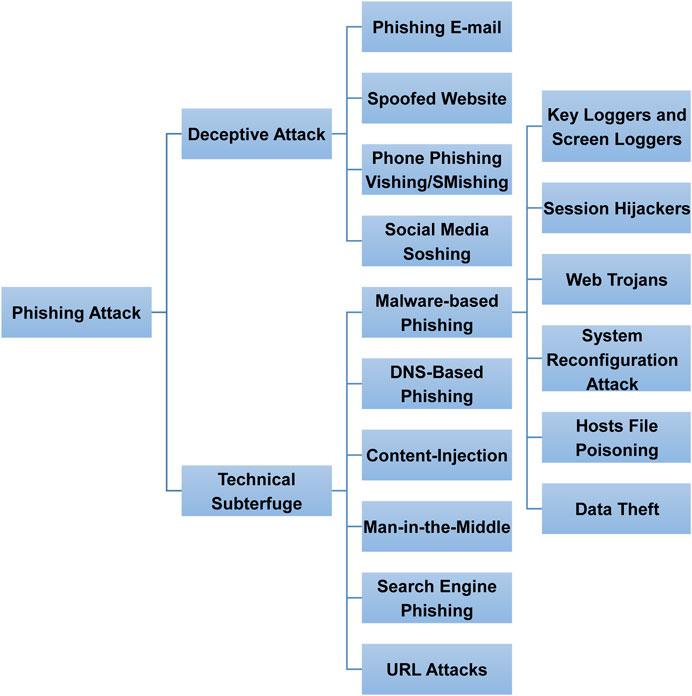
Frontiers Phishing Attacks: A Recent Comprehensive Study and a New Anatomy
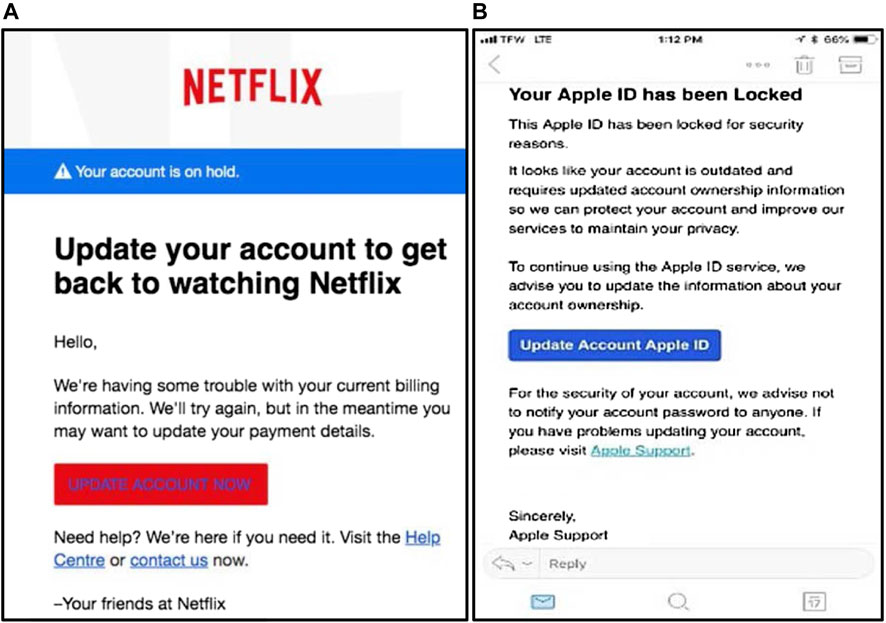
Frontiers Phishing Attacks: A Recent Comprehensive Study and a New Anatomy
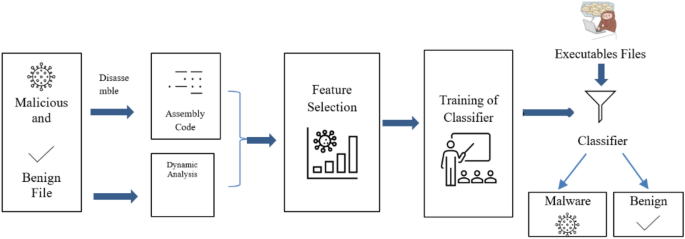
A Review on Malware Analysis for IoT and Android System

IT threat evolution Q2 2020. PC statistics - vulnerability database
de
por adulto (o preço varia de acordo com o tamanho do grupo)