Attackers use dynamic code loading to bypass Google Play store's
Por um escritor misterioso
Descrição
Threat actors rely on the 'versioning' technique to evade malware detections of malicious code uploaded to the Google Play Store
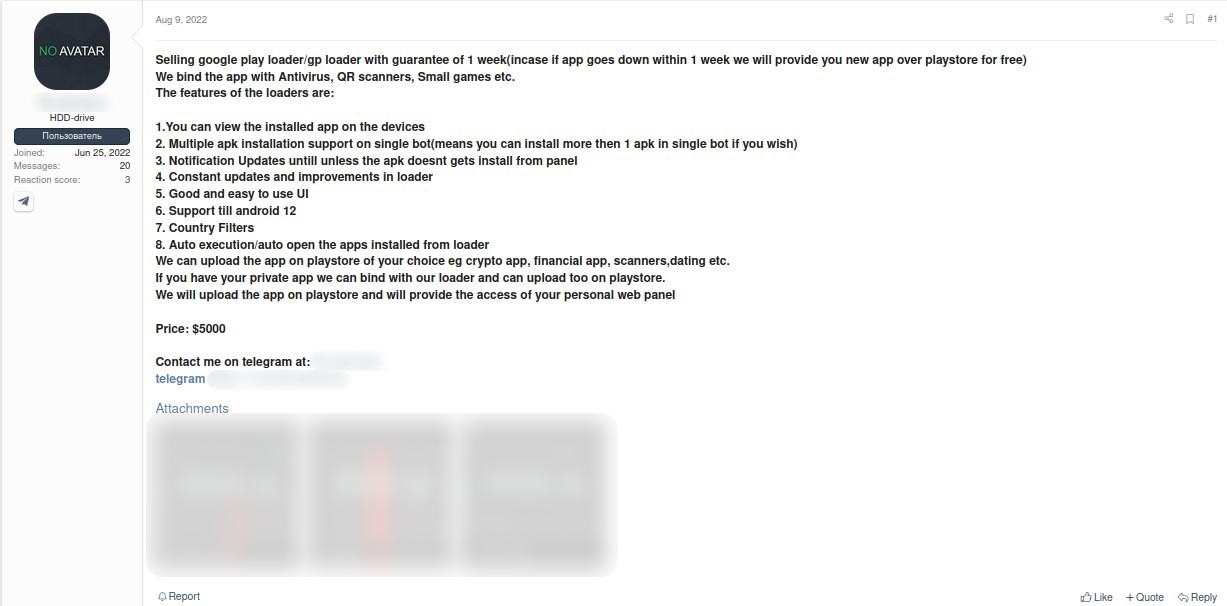
Google Play threat market: overview of dark web offers

Analysis of dynamic code updating in Android with security

Android: With Android 14, Google has a new plan to make your

Android and iPhone users get crucial Google Play and Apple App

Cyble — Hydra Android Malware Distributed Via Play Store

9 New Fake Apps on the Play Store Which Can Hijack SMS

Google describes how malware for Android can infiltrate the Google

Tool Release: Magisk Module – Conscrypt Trust User Certs

WakeUp Wednesday » Tesorion Cybersecurity Solutions

BrainTest - A New Level of Sophistication in Mobile Malware

Life cycle of Promon Shield's native library.
Bypass malware detection in Google Play Store with Dynamic Code

Cyble — Analysis - SharkBot Malware v1.63

The many lives of BlackCat ransomware
de
por adulto (o preço varia de acordo com o tamanho do grupo)